A security researcher named slipstream/RoL has discovered the Karma Ransomware, which pretends to be a Windows optimization program called Windows-TuneUp. What is worse is that this sample was discovered as software that would potentially be distributed by a pay-per-install software monetization company when people install free software downloaded from the Internet.
I have been railing against adware and PUA purveyors for quite some time and this continues to show how dangerous bundled software is becoming.
#Ransom Karma
— slipstream/RoL (@TheWack0lian) November 14, 2016
- 1/55, signed
- distributed via PUP bundling network
- possible indian origin
- clearnet c&c
hashes: https://t.co/YnSNbittiO pic.twitter.com/5kZr5tIRhp
If a user downloads and installs a free program that is monetized by this software monetization company, they would possibly be greeted with an offer for a Windows optimization program called Windows-TuneUp. While many people know these types of programs are not ones you want on your computer, there are unfortunately many who do not realize this. These people would then accept the offer thinking they are getting a program that will help optimize their slow computer.
When the program runs, they will be presented with a screen that shows various performance stats and tools to supposedly increase the performance of their computer.
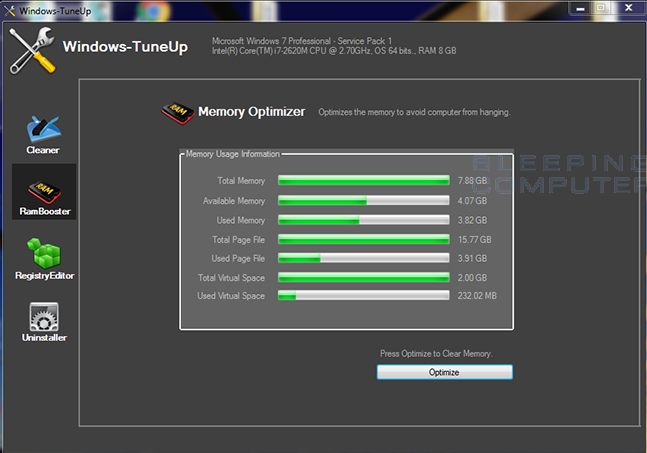
Also, if they had gone to the program's web site they would have been shown a web page that appears to look like a legitimate software company.
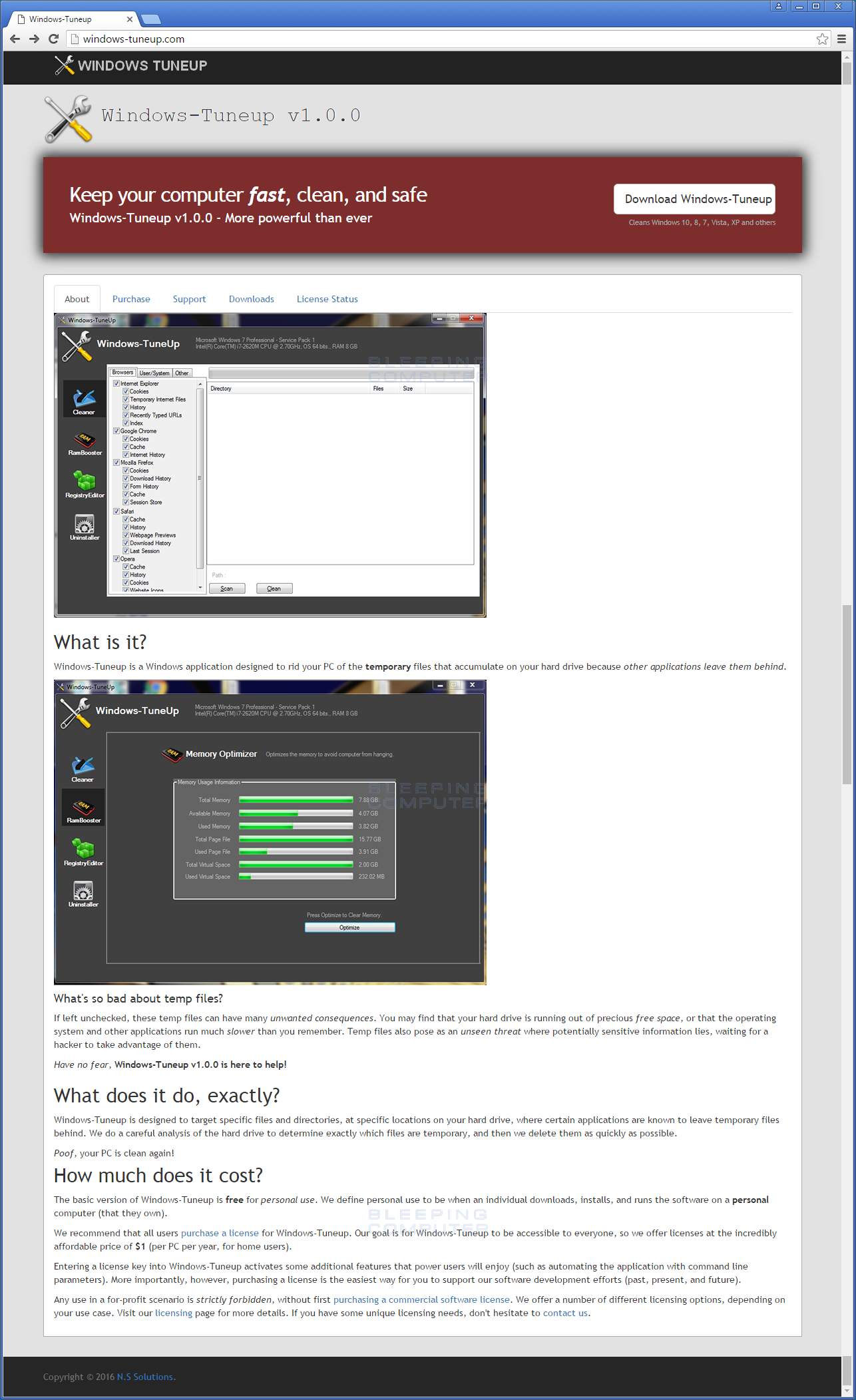
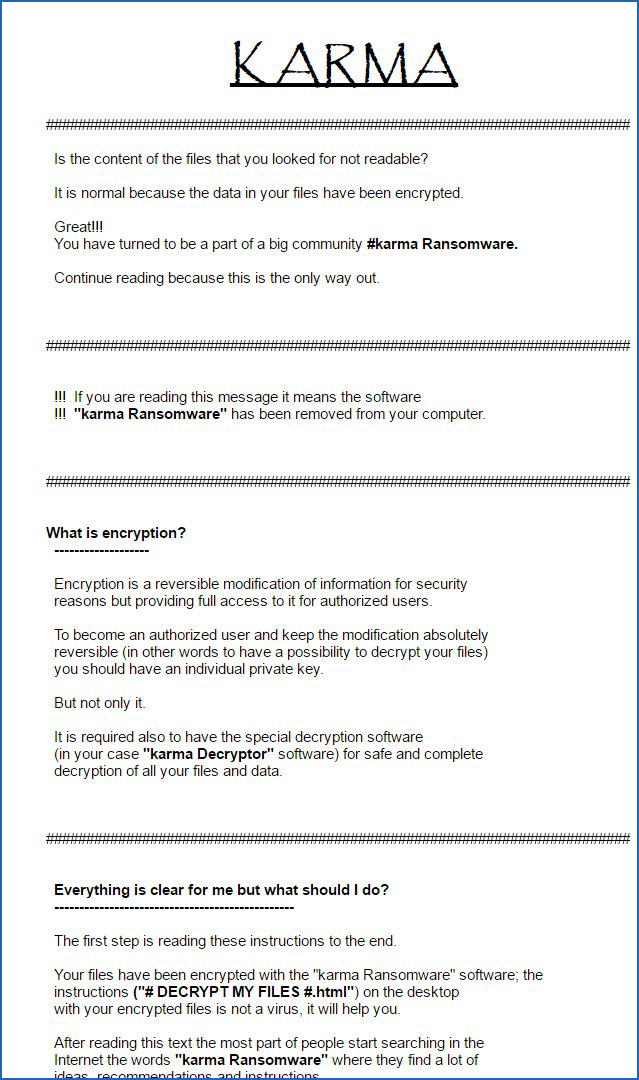
Unfortunately, this is just a ruse and while the victim's are playing with the fake program or reading the website, the program is silently encrypting the data on the computer and its connected drives. It is not until they are shown the Karma Ransomware's ransom note do they realize that they have been tricked and that their computer has a serious problem.
The good news is that this ransomware was very short-lived and the Command & Control server has already been shut down. Therefore, even if this ransomware is still being distributed, victims will not become infected.
It does, though, provide a very important lesson, which is anyone who downloads free software over the Internet should decline any offers that may be presented. In my experience, any offers being presented by free downloads are just not worth the headache they may present and should simply be avoided. Try instead to only download programs that are are adware and PUP free.
How the Karma Ransomware Encrypts a Computer
Thanks to MalwareHunterTeam, who deobfuscated the ransomware, I was able to get a closer look at the source code. When Karma is first executed it checks if the program is running on a virtual machine. If it is, it would terminate the program and state it is not compatible with the computer.
If it does not detect a virtual machine, it would connect to the Command & Control server to retrieve the encryption key that would be used to encrypt the victim's files. It will then search all drives, including connected network drives, for certain file types to encrypt. The targeted file extensions are:
.1cd, .3dm, .3ds, .3fr, .3g2, .3gp, .3gp2, .3gpp, .3pr, .7z, .7zip, .aac, .ab4, .abd, .acc, .accda, .accdb, .accdc, .accde, .accdr, .accdt, .accdu, .accdw, .ace, .ach, .acr, .act, .adb, .ade, .adn, .adp, .ads, .agdl, .ai, .aiff, .ait, .al, .amr, .aoi, .apj, .apk, .arj, .arw, .asax, .ascx, .asf, .ashx, .asm, .asmx, .asp, .aspx, .asset, .asx, .atb, .au, .avi, .awg, .back, .backup, .backupdb, .bak, .bank, .bay, .bdb, .bgt, .bik, .bin, .bkp, .blend, .bmp, .bpw, .bsa, .bz, .bz2, .c, .caf, .cash, .cdb, .cdf, .cdr, .cdr3, .cdr4, .cdr5, .cdr6, .cdrw, .cdx, .ce1, .ce2, .cer, .cfg, .cfn, .cgm, .cib, .class, .cls, .cmt, .config, .contact, .cpi, .cpp, .cr2, .craw, .crt, .crw, .cry, .cs, .csh, .cshtml, .csl, .csproj, .css, .csv, .d3dbsp, .dac, .das, .dat, .db, .db_journal, .db3, .dbf, .dbx, .dc2, .dcr, .dcs, .ddd, .ddoc, .ddrw, .dds, .def, .der, .des, .design, .dgc, .dgn, .dit, .djvu, .dng, .doc, .dochtml, .docm, .docx, .docxml, .dot, .dothtml, .dotm, .dotx, .drf, .drw, .dsw, .dtd, .dwg, .dxb, .dxf, .dxg, .edb, .eml, .eps, .erbsql, .erf, .exf, .fdb, .fdf, .ffd, .fff, .fh, .fhd, .fla, .flac, .flb, .flf, .flv, .flvv, .forge, .fpx, .fs, .fsi, .fsproj, .fsscript, .fsx, .fxg, .gbr, .gho, .gif, .gray, .grey, .groups, .gry, .gz, .h, .hbk, .hdd, .hpp, .htaccess, .html, .htpasswd, .ibank, .ibd, .ibz, .idx, .iff, .iif, .iiq, .incpas, .indd, .info, .info_, .ini, .ipsw, .iqy, .iwi, .jar, .java, .jnt, .jpe, .jpeg, .jpg, .js, .json, .k2p, .kc2, .kdbx, .kdc, .key, .kpdx, .kwm, .laccdb, .lbf, .lck, .ldf, .lha, .lit, .litemod, .litesql, .lock, .log, .ltx, .lua, .lzh, .m, .m2ts, .m3u, .m4a, .m4p, .m4v, .ma, .mab, .mapimail, .master, .max, .mbx, .md, .mda, .mdb, .mdc, .mdf, .mdp, .mdt, .mef, .mfw, .mid, .mkv, .mlb, .mmw, .mny, .money, .moneywell, .mos, .mov, .mp2, .mp2v, .mp3, .mp4, .mp4v, .mpa, .mpe, .mpeg, .mpg, .mpg, .mpga, .mpv, .mpv2, .mrw, .msf, .msg, .myd, .nd, .ndd, .ndf, .nef, .nk2, .nop, .nrw, .ns2, .ns3, .ns4, .nsd, .nsf, .nsg, .nsh, .nvram, .nwb, .nx2, .nxl, .nyf, .oab, .obj, .odb, .odc, .odf, .odg, .odm, .odp, .ods, .odt, .ogg, .oil, .omg, .one, .onepkg, .onetoc, .onetoc2, .orf, .ost, .otg, .oth, .otp, .ots, .ott, .p12, .p7b, .p7c, .pab, .pages, .pas, .pat, .pbf, .pcd, .pct, .pdb, .pdd, .pdf, .pdfxml, .pef, .pem, .pfx, .php, .pif, .pl, .plc, .plus_muhd, .pm, .pm!, .pmi, .pmj, .pml, .pmm, .pmo, .pmr, .pnc, .pnd, .png, .pnx, .pot, .pothtml, .potm, .potm, .potx, .ppam, .pps, .ppsm, .ppsm, .ppsx, .ppt, .ppthtml, .pptm, .pptm, .pptx, .pptxml, .prf, .private, .ps, .psafe3, .psd, .pspimage, .pst, .ptx, .pub, .pwm, .pwz, .py, .qba, .qbb, .qbm, .qbr, .qbw, .qbx, .qby, .qcow, .qcow2, .qed, .qtb, .r00, .r01, .r3d, .raf, .ram, .rar, .rat, .raw, .rax, .rdb, .re4, .resx, .rm, .rmm, .rmvb, .rp, .rpt, .rt, .rtf, .rvt, .rw2, .rwl, .rwz, .s3db, .safe, .sas7bdat, .sav, .save, .say, .sd0, .sda, .sdb, .sdf, .settings, .sh, .sldm, .sldx, .slk, .slm, .sln, .sql, .sqlite, .sqlite3, .sqlitedb, .sqlite-shm, .sqlite-wal, .sr2, .srb, .srf, .srs, .srt, .srw, .st4, .st5, .st6, .st7, .st8, .stc, .std, .sti, .stl, .stm, .stw, .stx, .svg, .swf, .sxc, .sxd, .sxg, .sxi, .sxm, .sxw, .tar, .tax, .tbb, .tbk, .tbn, .tex, .tga, .tgz, .thm, .tif, .tiff, .tlg, .tlx, .txt, .upk, .usr, .utorrent, .vb, .vbe, .vbhtml, .vbox, .vbproj, .vbs, .vcf, .vcproj, .vcs, .vcxproj, .vdi, .vdx, .vhd, .vhdx, .vmdk, .vmsd, .vmx, .vmxf, .vob, .vpd, .vsd, .vsix, .vss, .vst, .vsx, .vtx, .wab, .wad, .wallet, .war, .wav, .wb2, .wbk, .web, .wiz, .wm, .wma, .wmf, .wmv, .wmx, .wpd, .wps, .wsf, .wvx, .x11, .x3f, .xdp, .xis, .xla, .xla, .xlam, .xlk, .xlk, .xll, .xlm, .xlr, .xls, .xlsb, .xlsb, .xlshtml, .xlsm, .xlsm, .xlsx, .xlt, .xltm, .xltm, .xltx, .xlw, .xlw, .xml, .xps, .xslt, .xxx, .ycbcra, .yuv, .zip
When it encounters one of the above file types it would encrypt it using AES encryption and append the .karma extension to the filename. For example, test.jpg would become test.jpg.karma. While encrypting files, it would skip all folders that contain the following strings:
\$recycle.bin\
\$windows.~bt\
\boot\
\drivers\
\program files\
\program files (x86)\
\programdata\
\users\all users\
\windows\
\appdata\local\
\appdata\locallow\
\appdata\roaming\
\public\music\sample music\
\public\pictures\sample pictures\
\public\videos\sample videos\
\tor browser\
Finally, when it was done encrypting the files it will create ransom notes on the Desktop called # DECRYPT MY FILES #.html and # DECRYPT MY FILES #.txt and display them.
Last, but not least, it will create a Scheduled Task which will automatically start Windows-TuneUp.exe after it has been closed. This schedule task is called pchelper.
Files associated with the Karma Ransomware
Windows-TuneUp.exe
Registry entries associated with the Karma Ransomware
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer "auth"
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\ "Saffron"= "%Desktop%\\# DECRYPT MY FILES #.html"
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\ "Safron"= "%Desktop%\\# DECRYPT MY FILES #.txt"
IOCs:
SHA256: 6545ae2b8811884ad257a7fb25b1eb0cb63cfc66a742fa76fd44bddd05b74fe8
SHA256: cf5fda29f8e1f135aa68620ce7298e930be2cb93888e3f04c9cd0b13f5bc4092
Network Communication:
karma2xgg6ccmupd.onion
windows-tuneup.com/web293/xUser.php
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Comments
Amigo-A - 9 years ago
Cerber's offspring
Amigo-A - 9 years ago
Search returned no results of analysis Karma of VT and HA? I can get the results? Thanks.
humanfly - 8 years ago
We were just infected with this last week.
Latest version of McAfee installed, did not detect it. We called McAfee and escalated, they installed additional tools but were unable to detect it. I had expected they would like to add this signature to their antivirus database. Instead, they escalated me to an apartment that requested money to clean the machine, so I formatted.
We recovered 99% of data from backups but extremely recent data is encrypted. Wondering if there is any known method to decrypt?
thanks
dismalik - 6 years ago
Attention! Your computer has been attacked by virus-encoder!
All your files are now encrypted using cryptographycalli strong aslgorithm.
Without the original key recovery is impossible.
TO GET YOUR DECODER AND THE ORIGINAL KEY TO DECRYPT YOUR FILES YOU NEED TO EMAIL US AT: cryptomadbusiness@protonmail.com
It is in your interest to respond as soon as possible to ensure the restoration of your files.
Sr5xT9nbC7GkWKAJgCLN+mgvxYPzlUWRtj2n1+SKtq9vHUVTZJUwML2rGDoiBGXAHOKD/eJal40XWliQcDxZcc4bO80U0A3HoETfkW97zu7kD2Q4OlqdRMRpqvLSe/crg+xxRV7nlM6MY+PKHb5YlzOi3EMlX59cU7kR4kQwj3ha6rWe1L8OoLd56pfQ8+fkmIq2zbSJQsYnBx+X1Oq6tppLHniPZ2bZ20+vpNJboOozklwlFvboB8Y1qFlOmFpYOGVrYVaWg5iM7AmCxaBSoLAxB07G9xfCnO343FuZ1DiamjLvLkrCn3OjNrAspC4ScUxMHXZ34YFI5KwU4nwRXiSwuahx5JZ10Qhw1lzMEgIM/ewmpVKEvcmhJ3GOX6mdOnWIls9VwUy91izmtQJuqYw0KyJRXHs3j6hobsWv2kTRFYkhXoyjx34UIpyM96D6BZj1xWTaZv4IKYtRVGGdw2uPSQcPNBHmKVZzFceYUmHCE9YRcV2WrbG9BVJtl+K0CcFiQ+JdkcnwBmVpoXbHhJQ9dj/61fRzec1hyfFfaeBDyTnVnZcQe9uonV8PN7t/J0ylVXAFEm4lGdn7lHUCr4dgsgckME0Qf20J9a6FwZtWlW/SXpbBAjazAlzE5Uduwspqdq0GaUOKtQ3J9axY2GmCKwv5yq5o0mzC0eyGpaA=