
A new ransomware has been spotted over the weekend, carrying references to the Russian president and antivirus software. The researchers call it Nemty.
This is the first version of Nemty ransomware, named so after the extension it adds to the files following the encryption process.
The ransom demand
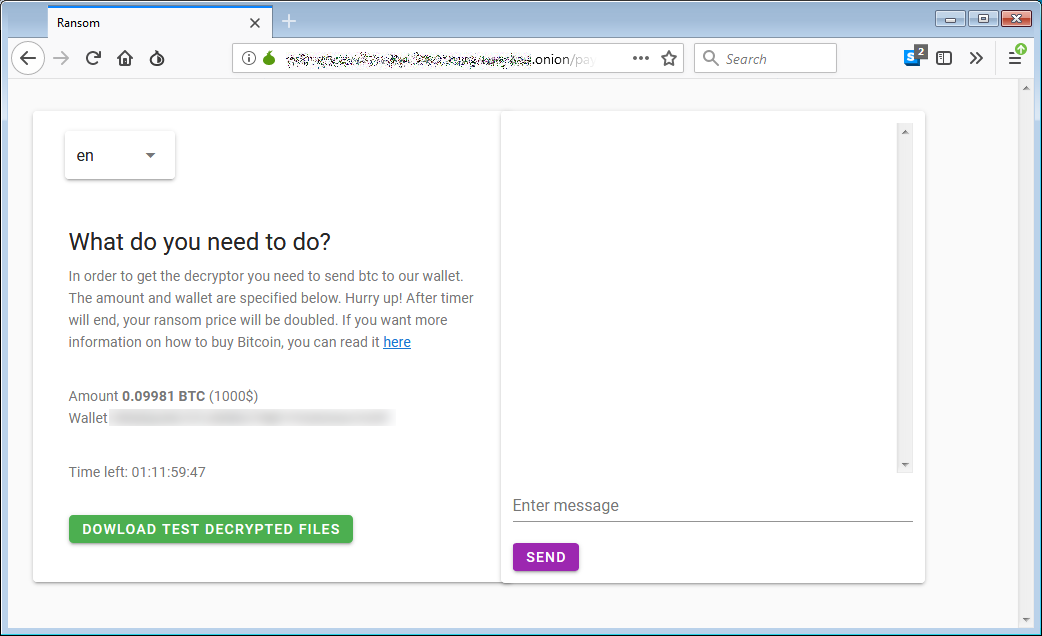
Like any proper file-encrypting malware, Nemty will delete the shadow copies for the files it processes, taking away from the victim the possibility to recover versions of the data as created by the Windows operating system.
Victims will see a ransom note informing that the attackers hold the decryption key and that data is recoverable for a price.
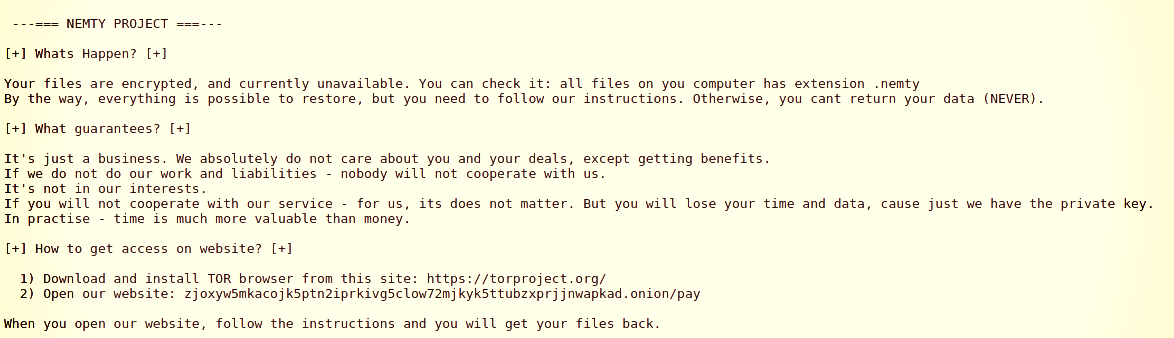
In BleepingComputer's tests, the ransom demand was 0.09981 BTC, which converts to around $1,000 at the moment.
The payment portal is hosted on the Tor network for anonymity, and users have to upload their configuration file.
Based on this, they are provided with the link to another website that comes with a chat function and more information on the demands.
Messages in the code
Security researcher Vitali Kremez took a closer look at the malware and noticed that it comes with an unusual name for the mutex object. The author called it "hate," as visible in the image below.
A mutually exclusive (mutex) object is a flag that allows programs to control resources by allowing access to them to one execution thread at a time.
Another weird thing Kremez noticed in Nemty's code is a link to this picture of Vladimir Putin, with a caption saying "I added you to the list of [insult], but only with pencil for now."
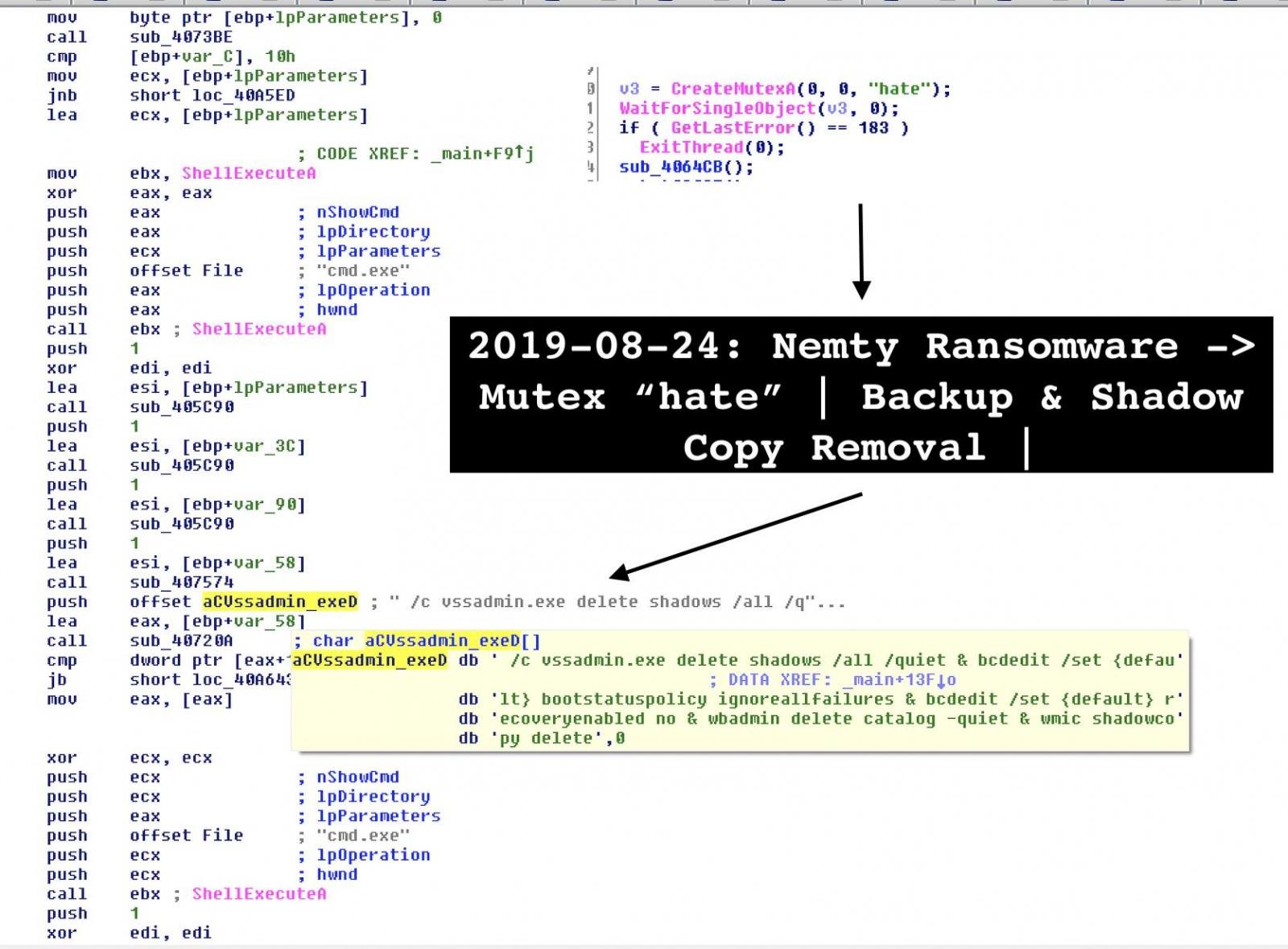
The list of peculiarities does not stop at this. A straight message to the antivirus industry was spotted by the researcher.
At first, the reference seemed an odd thing in the code but a second look at how Nemty worked revealed that it was the key for decoding base64 strings and create URLs is a straight message to the antivirus industry.
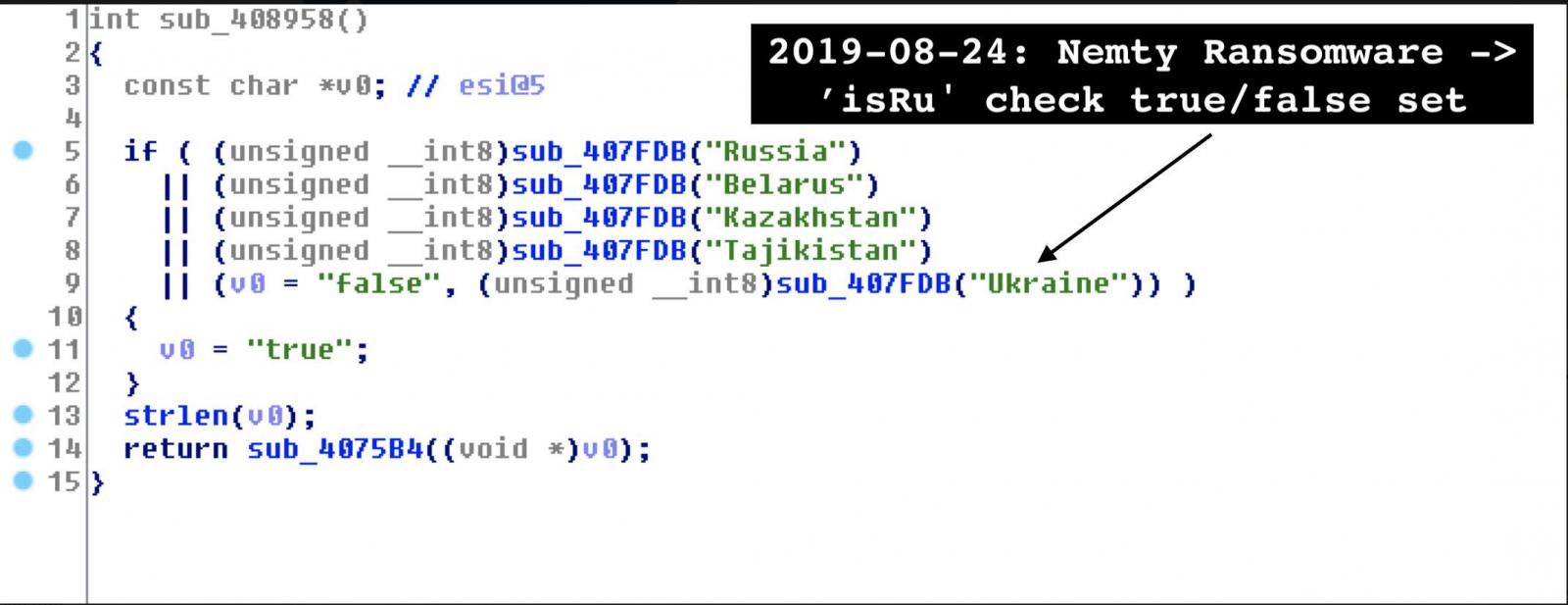
Another interesting thing is a verification Nemty makes to identify computers in Russia, Belarus, Kazakhstan, Tajikistan, and Ukraine. This is not to exempt the hosts from the file encryption routine, though, Kremez told BleepingComputer.
The "isRU" check in the malware code simply marks the systems as being in one of the five countries and then sends to the attacker data that includes the computer name, username, operating system, and computer ID.
It's unclear how Nemty is distributed but Kremez heard from a reliable source that the operators deploy it via compromised remote desktop connections.
Compared to phishing email, which is currently the common distribution method, leveraging a RDP connection puts the attacker in control as they no longer have to wait for the victim to take the phishing bait.
Kremez published his research notes on Nemty where he includes the list of folders (anything needed for booting the OS) and the file extensions (binaries, shortcuts, and log data) the malware does not touch.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now