
After analyzing millions of RSA keys and certificates generated on low entropy lightweight IoT devices, security researchers at Keyfactor discovered that more than 435,000 of them shared their prime factors making it easy to derive their private key and compromise them.
RSA keys are derived from random prime numbers (prime factors) and are used to securely transfer data to a remote source by encrypting it with the publicly available key, a process that only allows the remote source to decrypt the information using a private key.
While generating RSA keys isn't intrinsically insecure, their low entropy states could lead to the random numbers they generate being predictable as the Keyfactor research team was able to demonstrate.
"Lightweight IoT devices are particularly prone to being in low entropy states due to the lack of input data they might receive, as well as the challenge of incorporating hardware-based random number generation economically," the report says.
"Keys generated by lightweight IoT devices are therefore at risk of not being sufficiently random, increasing the chance that two keys share a factor and allow the key to be broken."
Critical systems at risk
If an attacker discovers the two prime factors used to derive the RSA keys, the private key can be re-derived, allowing the attacker to impersonate the remote data transmission source, as well as decrypt stored data that relies on the private key's confidentiality.
Compromised RSA keys expose a wide range of devices to compromise risks since they are currently used in traffic encryption within critical environments like home security systems, vehicles, industrial control devices, and even operating rooms.
"These weak keys expose users to a wide variety of harm, from disclosure of confidential information to failures of safety-critical systems," the researchers explain.
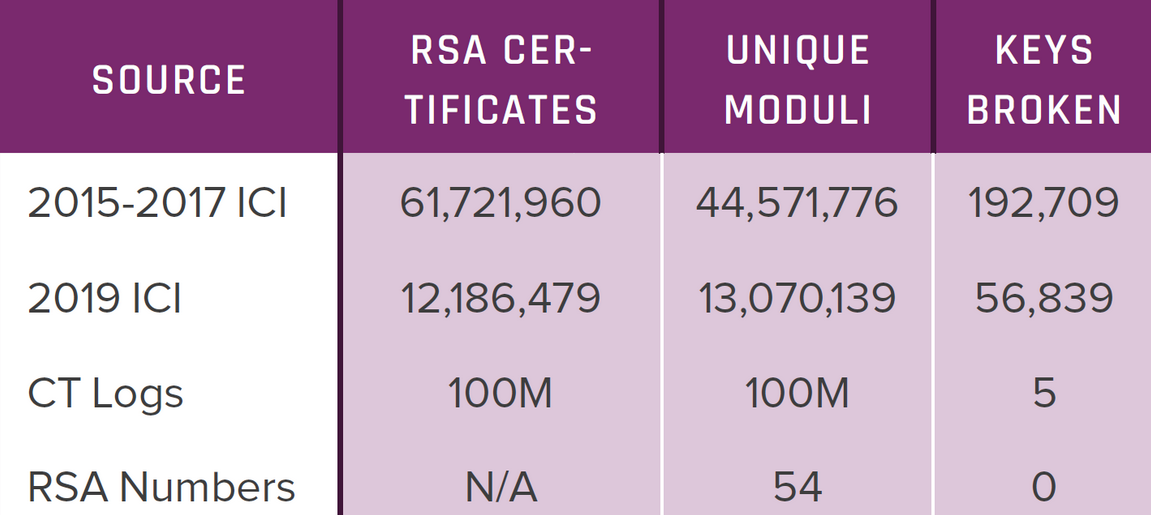
The researchers used a cloud-hosted Microsoft Azure virtual machine and a scalable GCD algorithm for shared factors to analyze a large collection of 175 million RSA certificates.
To harvest the RSA certs, they scanned the Internet to find 75 million keys actively used to encrypt traffic and also used around 100 million publicly available in Certificate Transparency logs.
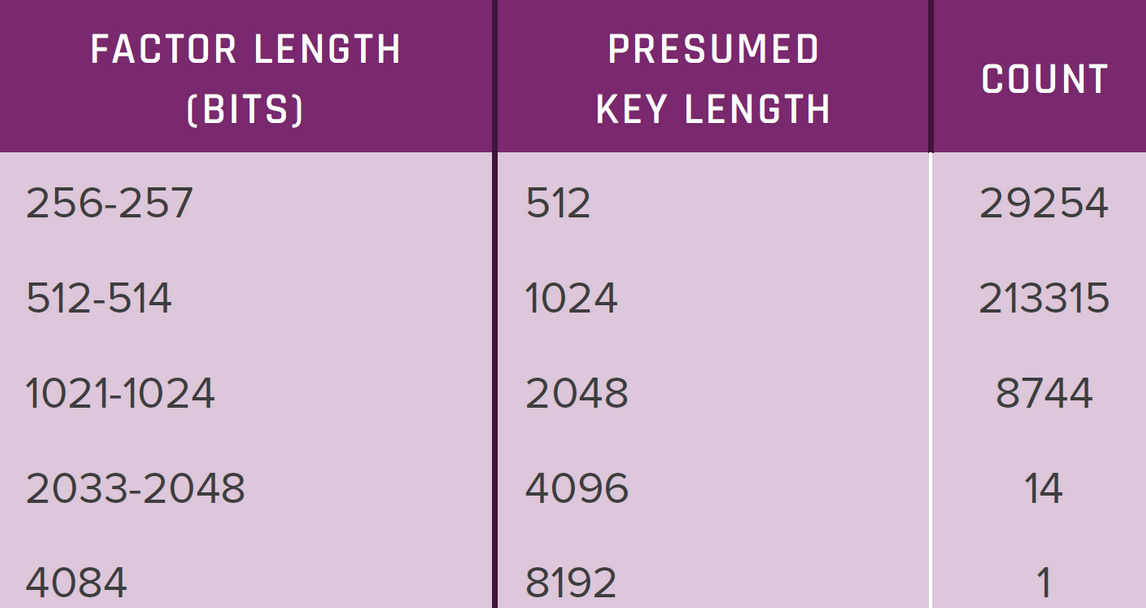
"The analysis reveals that at least 435,000 weak certificates – 1 in 172 of the certificates we found on the Internet – are vulnerable to this attack," they found.
Patching network IoT devices against this type of attack that could lead to key compromise is also quite tedious or even impossible for devices that don't support patching or are out of support, thus further increasing the risk of a future attack over a wider period.
Additionally, excluding the data collection costs seeing that some datasets are even available for free, the computation and development resources used for the study cost Keyfactor less than $3,000, a testament of the small investment needed to launch such an attack against actively used RSA keys.
Cloud services are readily available for rent to allow an adversary to both acquire and analyze the data efficiently. The only obstacle that an adversary truly faces in this attack is the implementation details. The attack itself has been well studied and understood, and the resources needed to execute it are now readily available at modest cost as well. To illustrate, development and computation resources spent for this study, excluding data acquisition, totaled less than $3000. - Keyfactor
"The findings are alarming. The research finds inordinate rates of compromise impacting IoT devices with design constraints and limited entropy," Keyfactor CTO Ted Shorter said. "These devices could include cars, medical implants and other critical devices, that if compromised, could result in life-impacting harm."
"In a real-world attack scenario, a threat actor with a re-derived private key for an SSL/TLS server certificate could impersonate that server when devices attempt to connect," Keyfactor senior integration engineer and researcher JD Kilgallin added.
"The connecting user or device cannot distinguish the attacker from the legitimate certificate holder, opening the door to critical device malfunction or exposure of sensitive data."
The security researchers released their findings at the First IEEE Conference on Trust, Privacy and Security in Intelligent Systems and Applications.
A copy of the 'Factoring RSA Keys in the IoT Era' research paper is available for download on Keyfactor's website.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Comments
Whalley_World - 6 years ago
As I see this: in a nutshell, there is no such thing as 100% secure. Anything considered "foolproof" simply hasn't met the right fool.
Having said that, I really feel that, in this day and age, there is no excuse whatsoever for manufacturers - IoT or anything else - to release a device without the possibility of installing security patches or other security measures to offset their known vulnerabilities.