
The U.S. Federal Bureau of Investigation (FBI) issued a warning to increase awareness on current e-skimming threats targeting both small and medium-sized businesses and government agencies that process online payments, as well as defense tips to fend them off.
E-skimming (also known as web skimming) is carried out by threat actors who inject malicious code in the form of payment card skimmer scripts within a website's payment processing platform, with the end goal of harvesting and stealing its customers' payment or personally identifiable information (PII).
"The bad actor may have gained access via a phishing attack targeting your employees—or through a vulnerable third-party vendor attached to your company’s server," the FBI says.
"Regardless, once he is in, he can load the malicious code and capture the credit card data in real-time as the user enters it. He either then sells the data on the darknet or uses it to make fraudulent purchases himself."
Defense measures against online skimming
The FBI and the Cybersecurity and Infrastructure Security Agency (CISA) provide [1, 2] a set of measures that government agencies and businesses can take to protect themselves against skimming threats:
• Change default credentials and create strong, unique passwords on all systems.
• Implement multi-factor authentication.
• Educate employees about safe cyber practices. Most importantly, do not click on links or unexpected attachments in messages.
• Segregate and segment network systems to limit how easily cybercriminals can move from one to another.
Businesses and agencies that operate e-commerce platforms can also turn on checks on third-party resource integrity via Content Security Policy (CSP) that will only allow JavaScript loading from a trusted list of domains, thus blocking attackers-controlled domains.
Subresource Integrity (SRI) is another option that allows them to prevent loading modified JavaScript code and only enabling legitimate resources using cryptographic hash checks.
Users, however, have a lot fewer options to protect themselves against online skimming attacks. Browser addons designed to completely block loading JavaScript code on untrusted websites are a choice but it doesn't help with whitelisted ones.
E-commerce users can report any suspected attacks to the local FBI office or directly to the FBI's Internet Crime Complaint Center at www.ic3.gov.
Web skimming is here to stay as shown by Magecart
Magecart groups, the most notorious threat actors behind e-skimming attacks, are highly effective cybercrime groups active since at least 2015, with a RiskIQ report saying that it goes back as far as 2010. They focus on Magento-powered e-commerce sites and operate campaigns that are just active as ever four years later, rarely showing any slowdown.
RiskIQ's head of threat research Yonathan Klijnsma said in a report detailing the expansion of Magecart activity to OpenCart and OSCommerce-powered online stores that "for every Magecart attack that makes headlines, we detect thousands more that we don’t disclose. A considerable portion of these lesser-known breaches involves third-party payment platforms."
"They’re currently focusing on payment data, but we’re already seeing moves to skim login credentials and other sensitive information. This widens the scope of potential Magecart victims far beyond e-commerce alone," also stated Klijnsma in an analysis of a large-scale operation against OpenCart online stores.
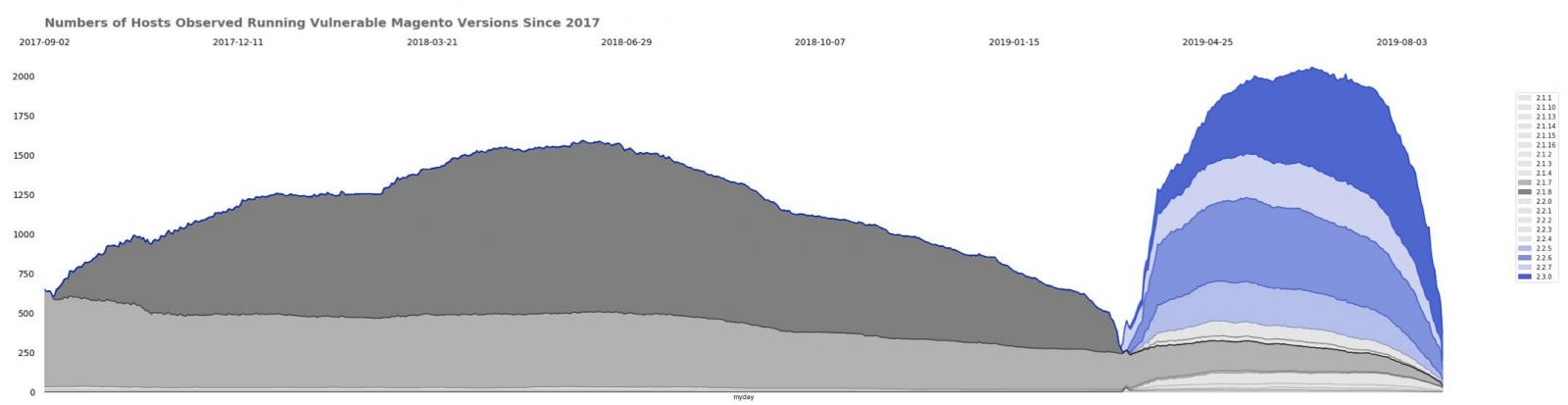
RiskIQ's Magecart report published this month estimates that this threat may have impacted millions of users, with the company's telemetry data showing a total of 2,086,529 instances of Magecart detections.
Magecart groups have been behind a card skimming campaign that successfully breached 962 e-commerce stores, a payment card skimming script injected within the PrismWeb-powered checkout pages of hundreds of online campus stores from U.S. and Canada, and have used an upgraded credit card stealer scripts designed to use an iframe-based phishing system as Malwarebytes security researcher Jérôme Segura discovered in May.
Another Magecart group developed a polymorphic Magecart skimmer script with support for 57 payment gateways that can easily be injected within almost any checkout page of any online shop to automatically start scraping customers' payment info without needing any customization as Sanguine Security researcher Willem de Groot found.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now