-
Linux Kernel Spectre Protection Changes to Boost App Performance
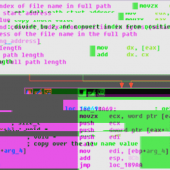
The Speculative Store Bypass Disable (SSBD) bit will be toggled off for programs that do not require the extra protection against the Spectre Variant 4 hardware security issue according to a proposed Linux kernel patch
- January 31, 2019
- 12:23 PM
 0
0
-
Escaping Containers to Execute Commands on Play with Docker Servers
Improperly secured privileged containers on the Play with Docker testing platform offered security researchers a way to escape Linux containers and run arbitrary code on the host system.
- January 14, 2019
- 12:56 PM
 0
0
-
New Webinar: Choose Your Own Investigation — Browser Attack Edition

Modern attacks have shifted focus to the browser, yet detection tools remain largely blind to the crucial activity happening there.
Join Push Security on February 11th for an interactive "choose-your-own-adventure" webinar on ClickFix, credential phishing, and other in-browser attacks we've observed in the wild.
-
U-Boot's Trusted Boot Validation Bypassed
Memory handling issues in U-Boot open-source bootloader for embedded devices make possible multiple exploitation techniques that lead to arbitrary code execution.
- November 06, 2018
- 03:12 AM
 2
2
-
New CSS Attack Restarts an iPhone or Freezes a Mac
A new attack has been discovered that will cause iOS to restart or respring and macOS to freeze simply by visiting a web page that contains certain CSS & HTML. Windows and Linux users are not affected by this bug.
- September 15, 2018
- 01:25 PM
 2
2
-
New "Turning Tables" Technique Bypasses All Windows Kernel Mitigations
Security researchers have discovered a new exploitation technique that they say can bypass the kernel protection measures present in the Windows operating systems.
- August 20, 2018
- 10:55 AM
 0
0
-
Two DDoS Friendly Bugs Fixed in Linux Kernel
Maintainers behind the Linux kernel have rolled out patches in the past weeks for two bugs that are just ideal for causing havoc via DDoS attacks.
- August 16, 2018
- 11:41 AM
 0
0
-
Multiple OS Vendors Release Security Patches After Misinterpreting Intel Docs
Almost all major OS vendors released security patches yesterday after a researcher discovered that some OS makers have misinterpreted an Intel CPU debug feature and left their systems open to attacks.
- May 09, 2018
- 09:10 AM
 4
4
-
Linux 4.16 Released. Kernel Release Was "Small and Calm"
Yesterday Linus Torvalds officially released Linux 4.16. In an announcement to the Linux Kernel Mailing List, Linus announced that this release of the Linux kernel was "small and calm", mostly related to networking, and that there was no need to continue testing it for another week.
- April 02, 2018
- 10:47 AM
 0
0
-
Meltdown Patch Opened Bigger Security Hole on Windows 7
Microsoft's Meltdown patch has opened an even bigger security hole on Windows 7, allowing any user-level application to read content from the operating system's kernel, and even write data to kernel memory.
- March 27, 2018
- 07:00 PM
 1
1
-
Microsoft February Patch Tuesday Fixes 50 Security Issues
Microsoft has released the February 2018 Patch Tuesday security updates, and this month's release comes with fixes for 50 vulnerabilities, along with additional patches for the Meltdown and Spectre vulnerabilities (ADV180002).
- February 13, 2018
- 02:42 PM
 1
1
-
LKRG: Linux to Get a Loadable Kernel Module for Runtime Integrity Checking
Members of the open source community are working on a new security-focused project for the Linux kernel. Named Linux Kernel Runtime Guard (LKRG), this is a loadable kernel module that will perform runtime integrity checking of the Linux kernel.
- February 04, 2018
- 06:33 AM
 1
1
-
Meltdown & Spectre Patches Causing Boot Issues for Ubuntu 16.04 Computers
Ubuntu Xenial 16.04 users who updated to receive the Meltdown and Spectre patches are reporting they are unable to boot their systems and have been forced to roll back to an earlier Linux kernel image.
- January 10, 2018
- 11:00 AM
 10
10
-
Linux Has a USB Driver Security Problem
USB drivers included in the Linux kernel are rife with security flaws that in some cases can be exploited to run untrusted code and take over users' computers.
- November 07, 2017
- 06:05 PM
 9
9
-
Patch Available for Linux Kernel Privilege Escalation
The Linux kernel team has released a patch to fix a security bug that could allow an attacker to execute code with elevated privileges.
- October 16, 2017
- 08:07 AM
 2
2
-
Linux Kernel Bug Reclassified as Security Issue After Two Years
Multiple Linux distros are issuing security updates for OS versions that still use an older kernel branch after it recently came to light that a mild memory bug was in reality much worse, and the bug was recently categorized as a security flaw.
- September 27, 2017
- 04:15 PM
 2
2
-
Attackers Can Bypass SKEL Protection in macOS High Sierra
A new security feature added in macOS High Sierra (10.13) named "Secure Kernel Extension Loading" (SKEL) can be bypassed to allow the loading of malicious kernel extensions.
- September 14, 2017
- 07:05 AM
 0
0
-
Bug in Windows Kernel Could Prevent Security Software From Identifying Malware
Malware developers can abuse a programming error in the Windows kernel to prevent security software from identifying if, and when, malicious modules have been loaded at runtime.
- September 07, 2017
- 02:25 AM
 3
3
-
Researcher Releases Fully Working Exploit Code for iOS Kernel Vulnerability
Adam Donenfeld, a researcher with mobile security firm Zimperium, has published today proof-of-concept code for zIVA — a kernel exploit that affects iOS 10.3.1 and previous versions.
- August 24, 2017
- 02:15 PM
 0
0
-
OpenBSD Will Get Unique Kernels on Each Reboot. Do You Hear That Linux, Windows?
A new feature added in test snapshots for OpenBSD releases will create a unique kernel every time an OpenBSD user reboots or upgrades his computer.
- July 05, 2017
- 06:22 PM
 4
4
-
New GhostHook Attack Bypasses Windows PatchGuard Protections
Security experts have discovered a method of bypassing Windows PatchGuard protections and hooking malicious code into the Windows kernel, which allows an attacker to plant rootkits on systems previously thought to be impregnable.
- June 22, 2017
- 06:35 PM
 0
0



 0
0