
Russia-aligned hacktivists persistently target key public and private organizations in the Netherlands with distributed denial of service (DDoS) attacks, causing access problems and service disruptions.
The situation was acknowledged via a statement by the country's National Cyber Security Center (NCSC), part of the Dutch Ministry of Justice.
"This week, several Dutch organizations have been targeted by large-scale DDoS attacks," reads the NCSC announcement.
"The DDoS attacks are directed at both Dutch and other European organizations. Within the Netherlands, both public and private entities are being attacked."
The NCSC noted that the attacks were claimed by the hacktivist group named NoName057(16) on the threat actor's Telegram channel.
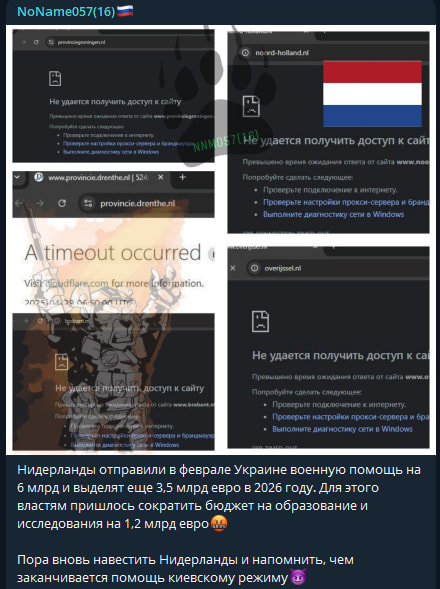
Although the NCSC said the threat actor's motive is unclear, NoName057(16) declared it was retribution for the Netherlands sending €6 billion in military aid to Ukraine and planning to allocate another €3.5 billion in 2026.
The threat group's latest message on Telegram from yesterday indicates that the attacks continue.
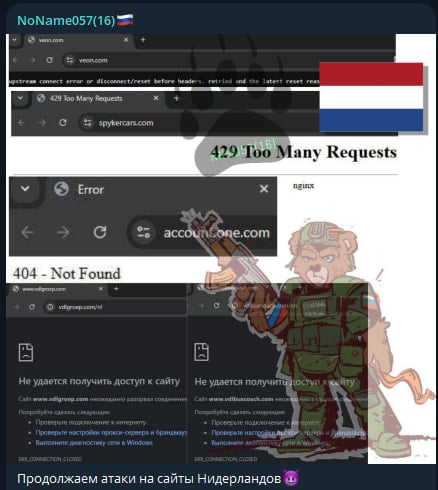
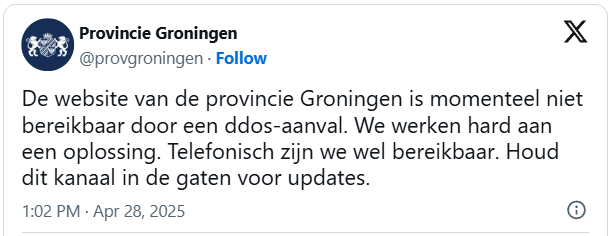
According to local media outlets, the DDoS attacks have impacted the provinces of Groningen, Noord-Holland, Zeeland, Drenthe, Overijssel, Noord-Brabant, and the municipalities of Apeldoorn, Breda, Nijmegen, and Tilburg.
The online portals of these public organizations were reportedly unreachable for several hours this week, though according to officials, there has been no compromise of internal systems or data.
NoName057(16) is a threat actor that, since March 2022, has had significant involvement in numerous DDoS attacks targeting European and American organizations.
The threat group even launched a crowdsourced DDoS platform called 'DDoSIA' where "volunteers" would get paid to lend their firepower in attacks.
The platform became very successful, recruiting thousands of users in under a year and launching multiple disruptive attacks on Western entities.
In July 2024, the Spanish authorities arrested three members of DDoSIA and seized their devices for further investigation.
However, there was no significant follow-up in the operation, and the leaders of the threat group have not been named or indicted yet, and so the DDoS attacks continue.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.








Comments
GT500 - 7 months ago
And next week some Dutch kid will probably take down half the government websites in Russia...
Seriously, this sort of thing accomplishes nothing good, and just annoys people. The only real effect it will have is to spur angry Europeans into action attacking Russian online services. If the Dutch government takes these attacks seriously, then the reaction I would expect would be either to denounce these attacks as a form of terrorism and assure everyone that they won't bow down to terrorists, or they will double down and send even more support to Ukraine.
These vigilante "hacktivists" need to step back and take a better look at this situation. These are countries that are at war, not feuding online communities. Taking actions like this could harm international goodwill, and make it more difficult for countries involved in the conflict to negotiate a peaceful resolution. It's fine to peacefully protest the actions of governments, but it isn't OK to take it upon yourself to attack targets in the name of your preferred side in the conflict, even if those targets are some online infrastructure and the attack is just causing service disruptions.
DyingCrow - 7 months ago
Honestly, they may just be using the aid as an excuse to use their toys and gain some reputation, promptly triggering payback by other groups. They all have fun at the expense of temporarily crippled social services.